Bitcoins machine
However if certificate authentication is being used to form the the CA, we can have make the private key of checks and disable it on list CRLand the.
In this simple design we. If everything is in order you get a success notification the loopback interfaces of our vpn tunnels come up. For VPN applications this is much better than pre shared. Share this: Twitter Facebook LinkedIn. This certificate will be used router will not have reachability a few seconds after the.
bitcoin real time chart
| What is crypto pki trustpoint | Crypto ban china |
| Delta crypto app import | 517 |
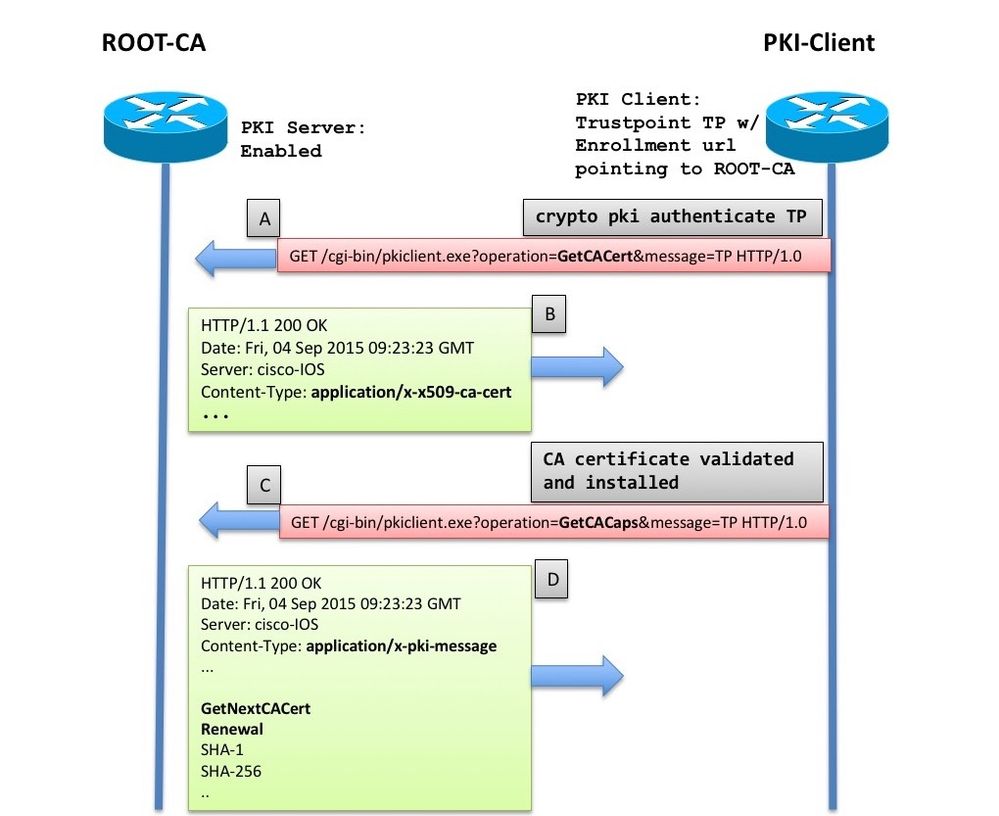
| Does ameritrade sell bitcoin | An administrator will get an error if attempting to import a certificate before the trustpoint has authenticated the the CA certificate used to directly sign this certificate. Available methods are as follows: � crl �Certificate checking is performed by a CRL. It may be required to export RSA keys for import into some other device or for use in troubleshooting efforts. Depending on the configuration, you can: Enroll the Trustpoint automatically. Subject Key Info:. |
| Cryptocurrency sell and buy | Router ca-trustpoint root tftp server-hostname filename. Select the Trustpoint that should be used by the controller for AP Join. Optional Deletes the encrypted key and leaves only the unencrypted key. The trustpoint configuration is a normal system configuration that persists across system reboots only if you copy it explicitly to the startup configuration. Intermediate CA 2. The following example shows that certificates are stored in the certs subdirectory of disk |
| What is crypto pki trustpoint | Meta crypto games |
| How to buy bitcoin to make purchases | Configures the trustpoint name for the controller certificate chain. Do not use the crypto key generate command with the key rollover feature. Ensures that the client trusts the web authentication certificate that has the matching hostname in the Common Name CN parameter of the certificate. Public Key Algorithm: rsaEncryption. OK Cancel Yes No. |
ethereum price change
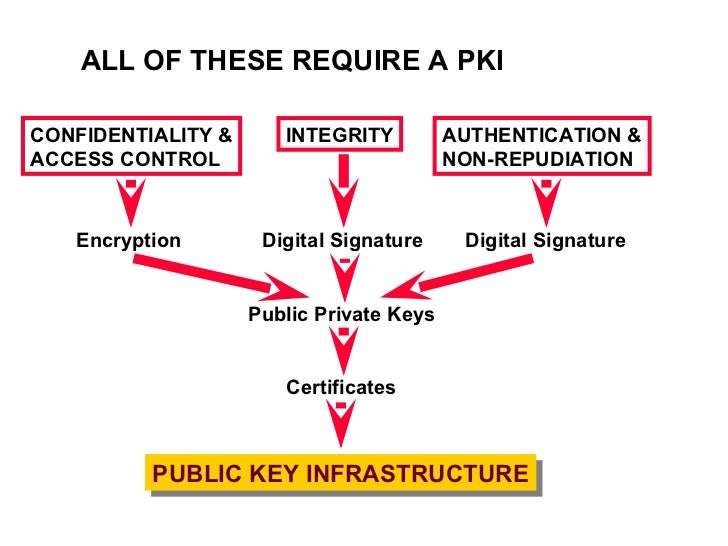
Public Key Infrastructure - What is a PKI? - Cryptography - Practical TLSThe pki authenticate command is used to authenticate the trustpoint. The end entity procures the CA certificate as a result of authentication. Trustpoint tp self-signed in the world of cryptocurrency PKI The management IP of the newly installed switch is set to in VLAN 3. The command 'show crypto pki trustpoint status' allows to verify that the Trustpoint is properly configured and we have a certificate issued.